With HSM speeds ranging from very low to enterprise level speeds and an ability to build redundancy to achieve high availability, we assist our customers to meet the most demanding requirements. Add-on tools allow our customers to perform centralised configuration and monitoring functions, configuration, load balancing, HSM scaling and many other functions.
Our customers have multiple business requirements for which we offer purpose fit solutions.
Areas of application of our solutions include the following:
The latest HSM has a comprehensive range of functions that supports the needs of the leading payment brands (American Express, Discover, JCB, Mastercard, UnionPay and Visa) in a number of areas including:
Our HSM solutions support all the main algorithms required for banking level encryption requirements, including:
Our HSM remote management tool helps reduce total cost of ownership by removing time spent in the datacentre and streamlining and minimising downtime needed with an HSM. Remote engagement with your HSM’s allows one to manage multiple HSM’s over distributed physical environments across the globe, thereby increasing the efficiency of distributed cryptographic infrastructure.
Safe connections, reduced travel time, expenses and lengthy passthrough procedures, near-zero data centre access and even faster delivering of updates are but some of the added benefits of managing your devices remotely and it is as secure as actually engaging with the HSM, if not safer!
Our HSM Monitoring tool:
Through the virtual console, the administrator has the ability to perform the same tasks as if he is in front of the HSM, with the benefit of working remotely. Security features such as the dual logins required to access the configuration application allows the administrator to safely access the HSM and perform standard or critical work as it is required. The remote management software also allows one to:
Through our HSM monitoring tool, alerts and status information is delivered automatically through a variety of interfaces including making the syslog data available to your SIEM solution while removing you from the physical presence to the HSM. This enables one to respond immediately should anything happen, which could range from a simple change to the HSM, to a critical incident. Each event can be categorized and allocated to a specific group for responsive action to be taken.
The monitoring solution refreshes the HSM’s utilization statistics every minute. Through role separation, our solution allows you to configure and channel information to various people such as high level alarms that would fall under the administrator’s responsibility, to statistics that are shared with the monitoring team. Critical events can be set to trigger an email notification to ensure immediate response from your engineers when you need it, while removing the burden of an entire team expected to monitor the system 24/7.
HSM performance can be monitored either individually or as part of a group to identify underutilized devices or potential bottlenecks in the environment. Devices monitored in groups allows one to retrieve information such as the top performing or underperforming devices by various functions, sensitivity, thresholds, and many other options. HSM’s monitoring provides the user with a wide variety of information such as general device information, device performance or device health.
All of this information is available through user interactive, information rich performance graphs via the dashboard which can also be printed and exported as the need arises.
Introducing our Remote Key Loading devices that seamlessly integrates with our HSM’s to provide an efficient, flexible and secure approach to managing and sharing critical keys remotely.
You can now securely manage your cryptographic keys into your HSM in a manner compliant with relevant security standards, including X9 TR-31, ANSI X9.24-1 and PCI PIN Security, to achieve operational flexibility without compromising security.
Keys are formed for multiple HSM’s distributed globally to create and distribute thousands of symmetric keys in a timely and secure manner while eliminating data entry errors. These keys can then be loaded and shared securely with the HSM through the use of a range of methods such as QR codes, smart cards, USB tokens and even paper components.
The remote key loading device also helps to improve efficiency through an easy to understand solution that simplifies key management and eliminates common data entry errors.
The device itself makes it so much easier to quickly share keys or information you need for easy entry into the device, and keys remain protected as it will erase immediately on tampering of the device.
To further improve security, you are now able to do away with key component storage after keys have been formed and shared as new key components are recreated on already installed keys if it needs to be shared and at a reduced cost.
Our devices also record the actions performed in a comprehensive audit log, together with the smartcard serial numbers used during the process – any attempt to modify log entries are detected which makes our remote key loading devices an outstanding benefit to any organisation.
Companies increasingly seek trustworthiness in devices, apps, and solutions to counter modern threats. To establish this trust, they rely on a single source to construct a robust security framework, facilitating secure connections by obtaining a “key” (Root of Trust). This key must be extremely secure and resilient by design to be inherently trusted.
The Root of Trust is critical in Public Key Infrastructure (PKI) for generating and safeguarding Root Certificate Authority keys, essential for tasks like software code signing and IoT device authentication.
Hardware Security Modules (HSMs) play a crucial role in creating a secure Root of Trust by generating, protecting, and storing cryptographic keys within a secure environment.
Hardware-based Roots of Trust are standard in highly secure sectors like finance and government due to their superior security features:
Our hardware-based HSMs come in various throughput options to match your transactional needs. Our expert engineers can assess your requirements and recommend the right device for your company.
Our Hardware Security Modules (HSMs) are ultra-secure devices that safeguard your sensitive data by handling encryption and signing keys within tamper-resistant hardware. They meet the strictest global Security & Compliance standards.
These HSMs are designed for cloud encryption, and their role separation ensures compliance. You can automate HSM management via REST API, saving time and eliminating the need for datacenter visits. HSMs can be partitioned to serve multiple applications or tenants, each with its own Local Master Key.
Our entry-level HSMs provide a cost-effective solution for developing and deploying custom code within a secure environment, making them popular among development teams for testing purposes.
We offer a range of HSMs, from low-speed entry-level devices for less active environments to high-speed enterprise-level devices capable of handling extensive transactions. As the Internet of Things drives demand for device IDs and certificates, our scalable HSM solutions can cluster for exponential processing power.
Our HSMs support a wide array of cryptographic algorithms, including high-speed elliptic-curve cryptography, ideal for compact computing environments. They are compatible with industry-standard operating systems and APIs.
In today’s complex digital landscape, businesses face growing compliance pressures and a heightened awareness of the need to enhance risk management and data protection measures. This urgency arises from the ever-present threat of cyberattacks, which often stem from internal vulnerabilities rather than external breaches. Such attacks can inflict significant costs on companies, including loss of customers, damage to their brand reputation, and regulatory fines.
Traditional perimeter defences and access controls, though widely used, often fall short in preventing these internal threats. They fail to safeguard data effectively, regardless of whether it’s in active use or not. This deficiency underscores the importance of a more robust data protection strategy.
This is where we come in. We prioritize the safeguarding of your most valuable asset—your data. Our innovative format-preserving tokenization solution goes beyond traditional data encryption, which secures data but can hinder its accessibility. Instead, our approach retains data in its original yet obscured format, allowing applications to present it in a user-friendly manner. Importantly, this method ensures that your data remains protected even in its usable format, rendering stolen data useless to unauthorized entities. This not only keeps you out of trouble but also safeguards your reputation, satisfies your shareholders, and pleases your customers.
Another challenge conventional systems face is protecting against manipulation by trusted individuals once they’re installed. We address this issue by setting up the solution initially and then removing the management tool from the environment. This prevents unauthorized manipulation and ensures that the system operates based on pre-configured rules agreed upon with your company. By eliminating the “keys to the castle,” we ensure that access to the system and rule manipulation are kept at bay
Additionally, in the realm of IT environments, encrypted data often requires decryption to remain usable. This occurs multiple times when data is in motion, passing between different security solutions and network layers. During these transitions, data briefly becomes vulnerable as it’s exposed in the open. Our data protection solution, however, prevents data from reverting to its clear form, maintaining its security throughout its journey within the network.
In summary, our comprehensive approach to data protection addresses the evolving challenges of the digital landscape, ensuring your data remains secure, accessible, and free from manipulation throughout its lifecycle.
Format-preserving tokenization, also known as encryption-based tokenization, secures data while keeping its original appearance intact.
This means it can maintain the data’s length, pad it as needed, stay within the same character set, or transform it into another format, among other possibilities
Classic encryption falls short because it doesn’t preserve the data format, making it challenging to use, especially in existing systems. Tokenization offers flexibility, with various methods and approaches available. Our solution’s algorithm is a perfect fit for safeguarding sensitive data elements. It delivers efficient and scalable tokenization, operates without the need for a central vault, and ensures there are no collisions. Importantly, all tokenization processes occur securely in memory and on the CPU, avoiding any interaction with disk storage, which enhances overall security.
Securing your data right from the start is essential. Our solution ensures automatic protection as soon as data enters your environment, regardless of the channel. We minimize data exposure throughout its lifecycle, only unlocking it when necessary and with your approval. Our format-preserving tokenization enables you to maintain operations and compliance while reducing risks.
Beyond data protection, our solution offers additional benefits like improved governance, compliance, and risk reduction.
Manage Risk and Security
Privacy & Compliance Benefits
Governance Benefits
Operational excellence
Companies are seeking cost-effective solutions that boost efficiency, reduce risk, and support remote work. Our document digitization and signing solution streamlines your processes, making them more efficient and secure. We employ digital signatures and bank-level encryption to safeguard your documents, whether it’s for basic tasks like leave approvals or complex, sensitive documents requiring multiple signatures.
In today’s flexible work environment, where both office and remote work are prevalent, we provide a solution that digitizes documentation and facilitates secure remote signing.
This ensures administrative processes continue seamlessly while maintaining document legality and non-repudiation. Our mobileresponsive platform eases administrative burdens
Our solution adheres to the latest security standards endorsed by governments and banks, making each transaction tamper-evident.
Consider the environmental impact: Sharing digital data is 31 times more cost-effective than physical copies, with documents often copied between 9 and 11 times. Reduce your carbon footprint by cutting paper and ink usage, minimizing waste from redundant cartridges, printers, and storage. Embrace a more eco-friendly approach, replacing numerous emails with a single notification.
Easily share files with clients and employees, ensuring efficient document sharing.
Embrace eco-friendly practices, appealing to environmentally conscious customers.
Reduce expenses on printing, equipment, paper, storage, and courier services.
Enable virtual work within the office, supporting employee flexibility.
Provide timely service with swift electronic document retrieval.
Safeguard documents from fire, theft, and unforeseen disasters, unlike paper records.
Ensure document authenticity with security features like OTP, Twofactor authentication, Geolocation, and Electronic certificates.
Maintain a comprehensive history of document-related events.
Store digital documents on secure off-site servers
Save time by reducing paper document handling and travel for signing.
Seamlessly connect with ERP or SharePoint environments via our service-oriented architecture (SOA) and APIs..
Replace physical storage with virtual storage for regulatory records and documents
Access and sign documents on mobile devices from anywhere, at any time.
Store documents in a regional cloud server or behind your company firewall for easy retrieval.
Access 24/7 support, 365 days a year, from accredited agents via our international call centre.
Digital Signatures
Send, sign, track and manage documents.
Digital Signing Service
The highest levels of global digital compliance.
Onboarding Systems Automated
onboarding forms & contracts.
Digital KYC
No-touch digital KYC and AML verification
Document Automation
Automate the flow of your documents
Contract Generation
Dynamic document generation with powerful
templates.
FaceTec 2D/3D FaceScans
proves the correct user is physically present by
matching them to their ID photo or 2D/3D FaceMap.
With mobile and cloud adoption on the rise, the traditional security perimeter has vanished, giving way to decentralized identities and the need for Zero Trust environments.
Securing the identities of workers, consumers, and citizens is paramount to prevent unauthorized access, data breaches, and fraud. Companies now demand that trust and security be ingrained in their infrastructure to ensure that only trusted users, systems, applications, and solutions gain access. This shift necessitates trust establishment before access, secure transactions, and ongoing trust maintenance.
Our Identity and Access Management solution forms a strong foundation for implementing a Zero Trust framework.
Trusted by Banking, Government, Healthcare, Insurance, Retail, and Education sectors globally, it’s tailored and highly secure for your environment.
We establish trust by providing secure user identities and credentials for enterprise applications, controlling access both on-premises and in the cloud. User and device authentication is mandatory for trust. We continuously monitor user behaviour and usage patterns to maintain trust throughout sessions.
Our Identity and Access Management solution relies on a trusted platform that underpins our actions, allowing sensitive operations and device checks. This includes device reputation assessment based on factors like Geolocation, ISP, mobile carrier detection, historical device fraud records, jailbreaking history, and account access velocity. Meeting these criteria grants access as a trusted device.
Credential issuance also involves stringent measures that users must pass before accessing the environment. User details are collected using a patented image capture process. Facial recognition and liveness testing undergo validation through over 50 forensic tests within seconds. Only upon passing these tests can a user and device access the trusted environment.

Companies increasingly seek trustworthiness in devices, apps, and solutions to counter modern threats. To establish this trust, they rely on a single source to construct a robust security framework, facilitating secure connections by obtaining a “key” (Root of Trust). This key must be extremely secure and resilient by design to be inherently trusted.

In addition to our core services, we offer a comprehensive suite of other supported solutions to ensure compliance with regulations like PCI DSS, SOX, and various privacy standards. Our commitment to excellence and technical expertise makes us a global leader in:
While our primary focus is in our core business, we recognize the importance of supporting our customers in related areas through trusted relationships. Our partners specialise in the following:
We provide a powerful and mature set of tools, enabling card issuers to prepare data for personalisation of smart cards for use in a wide range of applications, both financial and non-financial. The principal components of our issuance solution can be combined in several ways to satisfy the needs of both complete in-house card issuance and in-house data preparation only services. The components also integrate readily with card issuers legacy card management systems (CMS) and with personalisation systems that drive the printing (or loading) of such information onto smart cards.
Providing Magnetic Stripe encoding and Chip & Pin Test tools
Providing and Support of turnkey data preparation solution P3 Advanced and P3 Server
Providing an EMV (Eurocard, Mastercard, Visa) insurance solution

There are two typical configurations an end-to-end solution (for in-house issuing, batch and instant issuing) and an in-house data preparation solution with outsource card production (for external personalisation by a Bureau).
Both these Configurations reduce risk by allowing the issuer to keep control of its master keys (security in-house) and accommodate business innovation demands, flexibility and speed to market.
For those who need to upgrade from SDA to DDA cards, P3 server supports multiple crypto modules and RSA key generation and caching, enabling issuers to provide the same SLA (service levels) for DDA cards as for SDA cards.












“Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
If you need to issue EMV tokens (smartcards) to your customers for use in a wide range of applications, both financial and non-financial, or need to migrate from magstripe to Chip and Pin then we can help.
We provide a powerful and mature set of tools enabling card issuers to prepare data for personalisation of smart cards for use in a wide range of applications, both financial and non-financial. The principal components of issuance solution can be combined in several ways to satisfy the needs of both complete in-house card issuance and in-house data preparation only services. The components also integrate readily with card issuers legacy card management systems (CMS) and with personalisation systems that drive the printing (for loading) of such information onto smart cards.

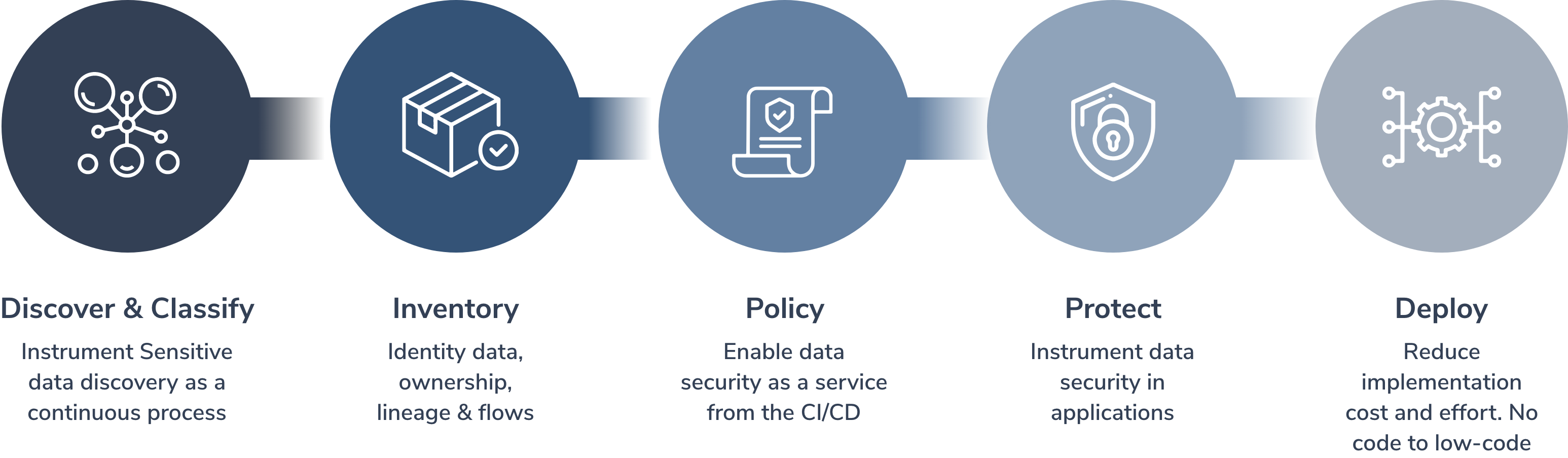
Managing cryptographic keys across multiple applications can become increasingly challenging as the key count rises. Manual and decentralized processes, aside from being costly, are prone to errors. Moreover, proving compliance is time-intensive, diverting attention from essential tasks.
A centralized key management solution automates key updates and distribution across various applications, offering benefits like symmetric and asymmetric key lifecycle management. This enables robust processes that ensure compliance with internal and external audits, fostering confidence in key management practices.
A lack of ownership, skilled personnel, and knowledge in isolated systems poses significant challenges to successful key management.
A well-implemented Cryptographic Key Management System mitigates these risks by assigning clear roles and responsibilities. This system automates manual tasks, allowing staff to focus on policy setting and efficient key delivery across systems. It not only lightens the workload securely but also facilitates compliance with standards like PCI-DSS and GDPR, enhancing competitiveness and business efficiency.
Our Cryptographic Key Management system is capable of providing the following advantages to any organisation that implements the solution:
Provides tamper evident audit and usage logs for proof of compliance
Central management of the cryptographic keys life cycle at large scale
Streamlines key management processes to reduce admin and travel costs
Automates key management activities and on-line key distribution
Reduces the risk of key compromise and human errors